The core components of Defense in Depth – The seven levels of the comprehensive security architecture
Vasi Tomoiaga >> 27 November 2024
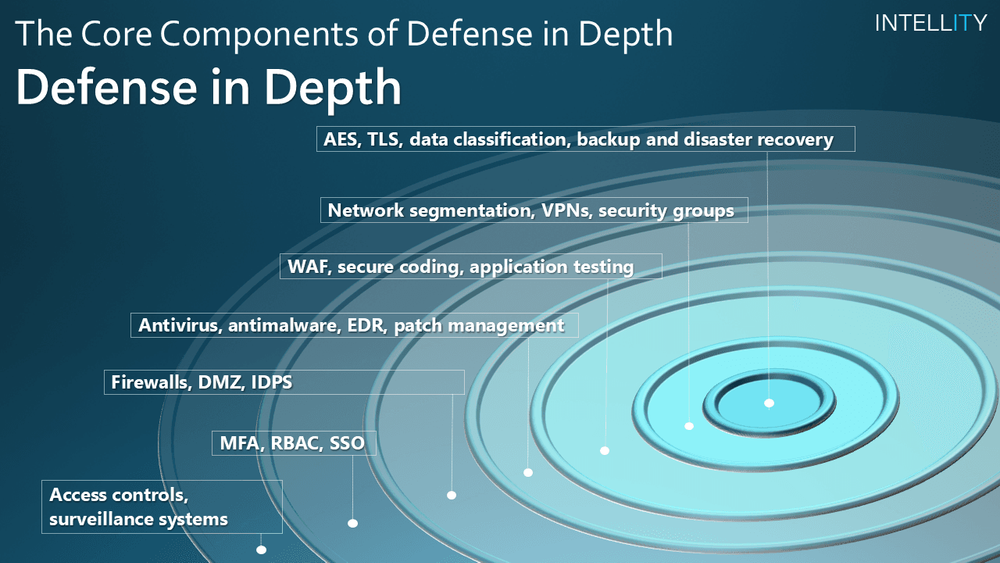
In the first part of this series, we introduced the concept of a layered security strategy, also known as "defense in depth," and examined its importance in today's digital world. In this second part, we will look at the seven core components of this strategy, which together form a robust defense against cyber threats. Each of these layers plays an essential role in protecting modern IT infrastructures - or poses risks if not consistently implemented.
1. Physical security – the basis of all protective measures
Physical security protects against unauthorized access to IT infrastructure and critical hardware.
Equipment: Access controls such as biometric scanners or RFID key cards secure sensitive areas.
Monitoring: Intelligent camera systems and alarm systems detect anomalies in real time.
Protective measures: Systems such as fire protection systems or redundant air conditioning protect against environmental hazards.
Everyday example:
An employee of a logistics company accidentally leaves the access door to the server room unlocked after work. An ex-employee takes this opportunity to steal important hardware. This leads to an outage of core systems for several hours and a significant delay in the supply chain.
Why important?
Physical vulnerabilities can undermine IT security measures. Even the best network is useless if the hardware is not protected.
2. Identity and Access Management (IAM) – Control over users and rights
IAM controls access to systems and data with clear rules and tools.
Multi-factor authentication (MFA): Combines something the user knows (password), has (token) or is (biometric).
Role-Based Access Control (RBAC): Limits rights to the minimum required for the role.
Zero Trust Principle: Verifies every access regardless of the user's location.
Everyday example:
An employee of a financial services provider uses a weak password that is cracked by an attacker using brute force attacks. The attacker gains access to internal customer data because multi-factor authentication was not activated. The company has to inform customers about the incident, which causes significant reputational damage.
Why important?
Stolen or unprotected credentials are one of the most common causes of security breaches.
3. Perimeter security – The protective wall of your network
Perimeter security protects the boundary between your internal network and external networks such as the Internet.
Next-Generation Firewalls (NGFWs): Analyze application-level traffic and block threats.
Demilitarized Zones (DMZ): Protect internal networks by isolating public services.
Intrusion Prevention Systems (IPS): Prevent intrusion attempts through signatures or behavioral detection.
Everyday example:
A medium-sized company that relies on outdated firewall technology falls victim to a ransomware attack that is introduced via an insecure remote desktop connection. Since there is no up-to-date IPS solution, the attack remains undetected for hours and production comes to a standstill.
Why important?
The edge of your network is the first target for external attackers – an unprotected perimeter is like an open door.
4. Network security – protection within the infrastructure
Network security prevents the spread of attacks within a corporate network.
Network segmentation: Separation of sensitive areas, such as financial or production systems, from the rest of the network.
Virtual Networks (VNets): In cloud environments, these enable the separation of workloads.
Network Security Groups (NSGs): Control inbound and outbound traffic based on IP addresses and ports.
Everyday example:
In an e-commerce company, an employee accidentally installs malware by opening a phishing email. Due to a lack of network segmentation, the malware is able to access the database servers and exfiltrate customer data.
Why important?
Internal attacks are often harder to detect. Network security makes it much more difficult for attackers to move around the network.
5. Computer security (endpoint security) – protecting every device
Endpoints such as laptops and smartphones are often the first attack surface.
Endpoint Detection and Response (EDR): Detects threats in real time and responds automatically.
Patch management: Regular updates close vulnerabilities.
Application Whitelisting: Allows only approved applications to run on a device.
Everyday example:
A field representative at a consulting firm uses a laptop with an outdated operating system. A known security vulnerability is exploited and the laptop is used to spread malware across the company network. It takes the company weeks to restore the systems.
Why important?
End devices are often unprotected – once infected, they can serve as an entry point for further attacks.
6. Application security – protecting your software
Application security secures your software from development to operation.
Secure SDLC (Secure Development Lifecycle): Integrates security testing into every step of software development.
Static Application Security Testing (SAST): Finds vulnerabilities in source code.
Runtime Application Self-Protection (RASP): Monitors and protects applications in live operation.
Everyday example:
A SaaS company overlooks a security flaw in an API used by third-party developers. Attackers exploit the vulnerability to gain unauthorized access to customer data, leading to contract terminations and claims for damages.
Why important?
Applications are a prime target for attackers. Vulnerabilities can have devastating consequences.
7. Data security – your most valuable asset
Data security protects sensitive information from loss or manipulation.
Azure Key Vault: Secures keys and passwords with HSM technology.
Encryption: End-to-end encryption protects data at rest and in transit.
Azure Backup: Automated backups enable quick recovery.
Everyday example:
An employee in an architectural firm saves sensitive customer projects on an unencrypted USB stick. The stick is lost and the customer data is unprotected and accessible to third parties. The customer then decides to go with a competitor.
Why important?
Data is the backbone of modern businesses. Its loss or compromise can have business-critical consequences.
Conclusion: Practical safety measures for everyday life
A multi-layered security strategy is not a luxury, but a basic requirement. Everyday incidents show how quickly companies become vulnerable due to seemingly small oversights. Systematically implement these seven layers to effectively protect your IT infrastructure and data.